DDOS Layer Explanaion
Short Intro for DDoS and popular layer attack explanation
DDOS Introduction
DDOS ( DIstributed Denied of Servies )
DDOS Segment Breakdown with OSI Model
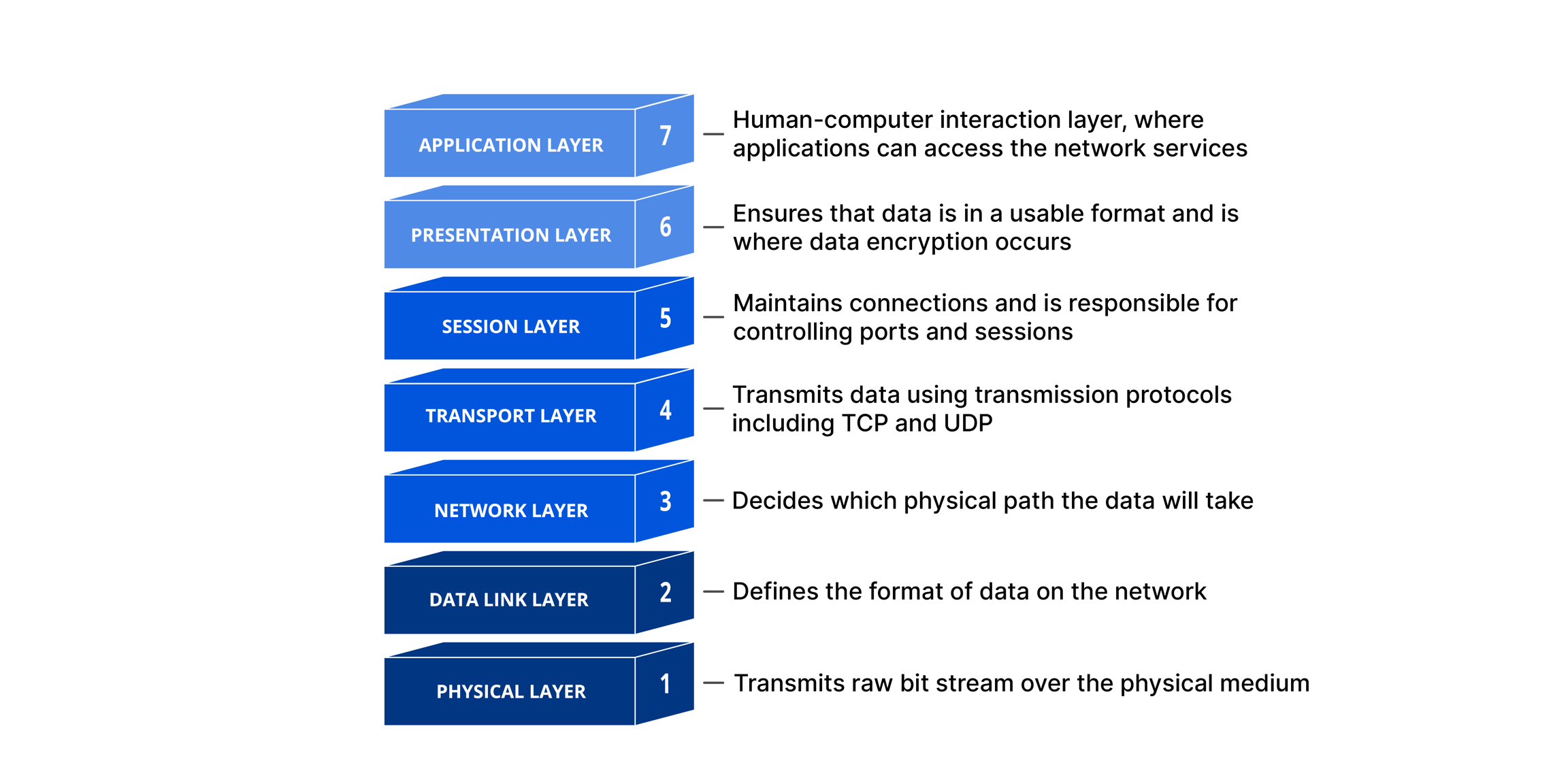
Popular Layer attacks Explanation
Layer 7 Attacks ( Application Layer )
Layer 7 attacks, also known as application layer attacks, target the top layer of the OSI model, which deals with application-level protocols such as HTTP, SMTP, FTP, and DNS. These attacks aim to exploit vulnerabilities in the application layer to disrupt or overwhelm a target server or application. Here are some examples of Layer 7 attacks:
GET Flood: This attack involves sending a large number of HTTP GET requests to a server, fenses and overload the target server.
RHEX (Random HEX): This attack sends random hexadecimal characters to a server, trying to exploit vulnerabilities in the server's parsing or processing mechanisms.
STOMP: This attack bypasses the "chk_captcha" mechanism, which is often used to protect against automated attacks by requiring users to solve a captcha.
STRESS: This attack sends HTTP packets with high byte values, potentially causing buffer overflows or other memory-related vulnerabilities in the target application.
DYN: This attack utilizes random subdomains in the HTTP requests, making it harder for mitigation systems to detect and block the attack.
DOWNLOADER: This attack involves reading data slowly from a server, consuming its resources over an extended period of time.
SLOW (Slowloris): This is an old method of DDoS attack that keeps HTTP connections open with the target server but sends requests very slowly, eventually overwhelming its capacity to handle concurrent connections.
HEAD: This attack specifically targets the HTTP HEAD method, which retrieves metadata about a resource, and can be used to exhaust server resources or exploit vulnerabilities related to HEAD requests.
Layer 4 Attacks ( Transport Layer )
Layer 4 attacks, also known as transport layer attacks, target the transport layer of the OSI model, which includes protocols such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol). These attacks aim to exploit vulnerabilities in the network and transport layers to disrupt or overload a target server or network. Here are some examples of Layer 4 attacks:
TCP Flood Bypass: This attack floods a target server with a high volume of TCP packets, overwhelming its capacity to handle incoming connections or consuming its network resources.
UDP Flood Bypass: Similar to TCP Flood, this attack floods the target server with a high volume of UDP packets, causing network congestion or consuming its resources.
SYN Flood: This attack exploits the three-way handshake process of the TCP protocol by sending a large number of SYN packets to the target server, exhausting its resources and preventing legitimate connections.
CPS (Connection Per Second): This attack involves rapidly opening and closing connections with a proxy server, consuming its resources and potentially causing it to become unresponsive.
ICMP (Internet Control Message Protocol): ICMP flood attacks involve sending a high volume of ICMP echo request packets to a target server, overwhelming its network capacity and potentially causing network latency or downtime. Note that ICMP is a layer 3 protocol, but it can be included in layer 4 attacks.
CONNECTION: This attack aims to keep connections alive with a proxy server, consuming its resources and potentially causing it to become overwhelmed.
VSE (Valve Source Engine Protocol): This attack targets the Valve Source Engine protocol, commonly used in online gaming, by sending malicious packets to disrupt or overload game servers.
Teamspeak 3 (TS3): This attack utilizes the Teamspeak 3 status ping protocol to send a high volume of status ping requests to a Teamspeak server, causing resource exhaustion or disruption.
FiveM (FIVEM): This attack targets FiveM servers, which are used for multiplayer modifications in the game Grand Theft Auto V, by sending status ping requests to overload the server.
Amplification Attacks: These attacks involve leveraging certain protocols or services to amplify the volume of traffic sent to the target, causing network congestion and disrupting services. Examples include Memcached, NTP, DNS, Chargen, CLDAP, Apple Remote Desktop (ARD), and Remote Desktop Protocol (RDP) amplification attacks.
Layer 3 Attacks ( Network Layer )
Layer 3 attacks typically exploit vulnerabilities in network protocols and infrastructure. These attacks may involve manipulating routing tables, forging IP addresses, or exploiting weaknesses in the way networking protocols function.
Network Congestion: Overwhelming the target's network capacity with a high volume of traffic, leading to congestion and potential service degradation.
Fraggle Attack: Overloads the target's resources with a high volume of UDP echo traffic, leading to decreased network performance
DNS Amplification: Abuses DNS resolvers to amplify traffic, overwhelming the target's resources and potentially causing service degradation
SYN/ACK Flood : Floods the target with SYN or ACK packets, exhausting connection resources and causing service disruption.
BGP Route Hijacking: Redirects traffic through a malicious network, facilitating more efficient DDoS attacks and complicating mitigation
Ping of Death: Disrupts target systems by sending malformed ICMP packets, potentially causing crashes or unresponsiveness
Session Hijacking: Attackers intercept and take control of established sessions between two parties, gaining unauthorized access to sensitive information or resources.
Man-in-the-Middle (MitM) Attacks: The attacker secretly intercepts and relays communication between two parties, compromising confidentiality and potentially manipulating data.
Session Fixation: Attackers set or fix the session identifier to a known value, allowing them to hijack a user's session after authentication, leading to unauthorized access.
Denial of Session (DoSes): Overwhelming session establishment or management mechanisms, preventing legitimate users from establishing sessions and disrupting services.
Session Timeout Attacks: Exploiting vulnerabilities in session timeout settings to keep sessions alive longer than intended or forcing premature session termination.
Session Redirection: Forcing a user's session to be redirected to a different destination controlled by the attacker, leading to potential phishing attacks or unauthorized actions.
SSL Stripping: Downgrading a secure HTTPS connection to an unencrypted HTTP connection, exposing sensitive information and compromising data confidentiality.
Layer 5 Attacks (Session Layer)
Layer 5 attacks exploit weaknesses in session management, potentially resulting in unauthorized access, data breaches, or service disruptions. Implementing secure session practices, strong authentication, encryption protocols, and monitoring for suspicious behavior are crucial for mitigation. Regular security audits and updates help maintain a robust defense against Layer 5 attacks.
Session Hijacking: Attackers intercept and take control of established sessions between two parties, gaining unauthorized access to sensitive information or resources.
Man-in-the-Middle (MitM) Attacks: The attacker secretly intercepts and relays communication between two parties, compromising confidentiality and potentially manipulating data.
Session Fixation: Attackers set or fix the session identifier to a known value, allowing them to hijack a user's session after authentication, leading to unauthorized access.
Denial of Session (DoSes): Overwhelming session establishment or management mechanisms, preventing legitimate users from establishing sessions and disrupting services.
Session Timeout Attacks: Exploiting vulnerabilities in session timeout settings to keep sessions alive longer than intended or forcing premature session termination.
Session Redirection: Forcing a user's session to be redirected to a different destination controlled by the attacker, leading to potential phishing attacks or unauthorized actions.
SSL Stripping: Downgrading a secure HTTPS connection to an unencrypted HTTP connection, exposing sensitive information and compromising data confidentiality.
Last updated
